Securing your business starts with understanding your cyber risks. For most organizations, humans are the biggest risk of all — and social engineering is one way that cyber criminals exploit that reality.
Discover what social engineering is, how and why these attacks work, and steps you can take right now to strengthen your defence against social engineering scams.
What is social engineering?
Social engineering describes a broad range of manipulative interactions and techniques that cyber criminals use to trick their victims into doing something — launching malware, disabling systems, or sharing private information — that advances the attack.
Social engineering is one of the easiest, cheapest, and most popular cyber attacks — with Verizon’s 2021 Data Breach Investigation Report acknowledging a major jump in social engineering breaches in the past year and an overall upward trend since 2017. There are a few reasons why social engineering reigns.
The first is that cyber crime actors are usually trying to bring in money. As businesses spend more on automation, testing, and cyber security best practices, there are fewer IT vulnerabilities for attackers to exploit.
So, instead of targeting technological weaknesses such as outdated software, attackers take advantage of the one vulnerability still typical in all companies: the people.
The second reason is that social engineering is effective. Humans aren’t perfect — we’re busy and might forget or not have time to follow cyber security best practices. Attackers have their social engineering tricks down to a science, relying on the same attack methods and techniques that have worked for years.
4 types of social engineering attacks
To recognize and defend against social engineering, your team needs to know what to look for. Many cyber attacks rely heavily on social engineering — these are the key ones to know.
1. Phishing, vishing, and smishing
Phishing attacks rely on social engineering techniques to lure users into clicking on a malicious link or file in an email. These scams are common because they’re relatively simple to execute. Even the most inexperienced cyber attackers can find and purchase phishing kits — collections of malicious tools used to launch these types of attacks — without much trouble.
The attacker targets a broader group expecting that some emails will bypass spam filters and technical protections. Of those emails that get through, a small percentage of victims may fall for the bait.
Phishing emails may look something like this:
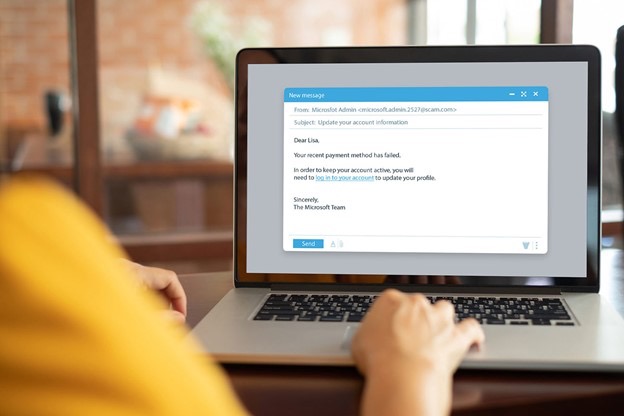
Clicking the link may open an illegitimate website prompting the victim to enter their username and password, revealing both to the attacker. Alternatively, clicking the file could launch malware that infects the victim’s device or network.
These attacks can cause extreme damage too. In 2021, a healthcare employee fell victim to a phishing email. According to the two-month-long investigation, the Revere Health employee clicked a link in the malicious email that gave the attacker remote access to their account. The incident exposed confidential data for 12,000 patients, compromising medical record numbers, dates of birth, health provider names, procedures, and insurance provider names.
This type of cyber attack typically happens via email, like in the example above, but hackers are starting to use other mediums. In fact, the term has evolved: “vishing” refers to phone call-based phishing and “smishing” for scams by text message.
Robinhood, the online trading platform, was recently the victim of vishing. The hacker social engineered a customer service representative by phone and compromised sensitive data for about 7,000,000 Robinhood customers.
2. Spear phishing
Instead of casting a large net hoping someone will fall for the trick, spear phishing involves very deliberate and strategic targeting. The attacker employs similar social engineering tactics used in phishing but with more preparation.
Before diving into the details, here’s a simplified overview of how spear phishing attacks work:
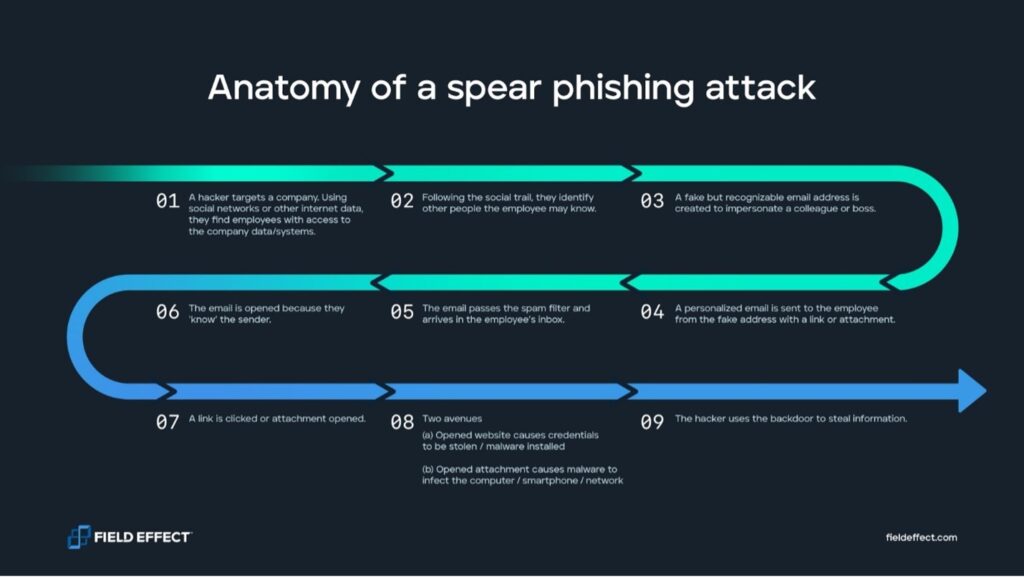
Prior to launching the attack, the cyber criminal takes several preliminary steps.
First, they target and research a specific company. Imagine the attacker belongs to a state-sponsored cyber crime group, and their goal is to steal classified corporate data. The hacker may scour social networks to find an employee that works closely with said data at the organization. How long the hacker takes to research the victim depends on their goal and the nature of the attack.
With this target in mind, the attacker will follow the social trail to identify that person’s colleagues, the name of the department they work in, the title of their supervisor, and more. Attackers go to extreme lengths to make their attacks look as authentic as possible. They may go so far as to register a domain name similar to their target organization and create an email address under it.
One common trick is a deliberate typo in the domain name. For example, instead of “organization.com,” it might be “orgamization.com.” A busy employee might not notice that typo unless they’re actively looking for it.
With all these elements in place, the cyber criminal stages an attack by sending a malicious email to the user they’re targeting. Because of how personalized and authentic the message is, it’s far more likely the user will click on the link — and from there, the rest of the attack will play out like a normal phishing attempt.
Spear phishing at the heart of the Twitter attack
In 2020, hackers targeted Twitter employees in a sophisticated phone spear phishing campaign. The scam worked, and the hackers accessed the social media accounts of several high-profile figures and corporations, including Barack Obama, Elon Musk, and Apple.
The attackers tweeted from many accounts, sharing a bitcoin scam that brought in more than USD $100,000.
According to an update posted on Twitter’s blog, the hackers targeted a small number of employees via phone. The company explicitly says that the attack “relied on a significant and concerted attempt to mislead certain employees and exploit human vulnerabilities to gain access to our internal systems.
3. Business email compromise
Business email compromise (BEC) is a scam that relies heavily on social engineering techniques. The cyber attacker poses as or impersonates someone else, typically a company executive or third-party vendor, to initiate financial transfers to an account they control.
But to pose as an executive or vendor, they need a disguise.
Attackers need access to the right account, or at least similar credentials, to make the transfer look realistic. Regardless of how they gain access or who they impersonate, attackers spend time gathering information to make their communications seem authentic, much like a spear-phishing attack.
The attacker then uses this account, as the true user would, to send email messages and interact with others in the organization. This disguise gives the attacker incredible power. It allows them to take advantage of the trusting relationship with the victim’s colleagues and skip many technical protections intended to prevent an attack.
How common is business email compromise?
According to the FBI’s Internet Crime Report 2020, BEC schemes are incredibly damaging, with 19,369 complaints costing businesses approximately $1.8 billion. There were far more complaints about phishing — more than 240,000 — however losses for those totalled only $54 million.
4. Watering hole
During a watering hole attack, the hacker compromises a legitimate website their target is likely to visit instead of attacking them directly, like most social engineering attacks. Here’s how it works.
The cyber criminal starts with reconnaissance. They’ll research the organization or industry they’re targeting and use this information to find websites they frequent, such as discussion boards or forums. This is where the name comes from — attackers find and prey on the target’s “watering hole.”
Then, the attacker finds and exploits vulnerabilities on the website to inject malware. Once this is done, simply visiting the compromised website will infect users with malicious code, potentially giving the attacker access to the victim’s account. Users may not even realize they’ve been hacked.
Common social engineering techniques
Impersonating authority figures or a trusted person — attackers may pose as an executive the victim knows, such as the CEO. Disguised as someone else, the attacker may request a wire transfer, company credentials, or other confidential information.
Preying on the victim’s need for information — attackers may encourage a victim to open their email by falsely offering new information. By designing the scam to pique curiosity, the recipient may be more likely to open files or links to gain that information.
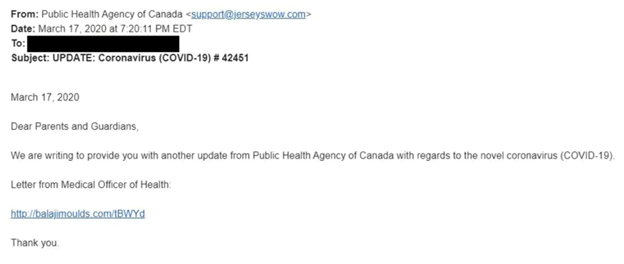
[Source: CBC]
Using fear or urgency to pressure action — attackers create social engineering scams with limited time offers or tasks requiring urgent action. Despite knowing better than to open a link without first inspecting it, victims may follow directions haphazardly if pressured to act quickly.
Hiding their attack within current events — attackers know that governments and organizations send communications about current events, often with consistent email branding and messaging. This consistency is easy for attackers to copy and use for malicious purposes.
Countermeasures to defend against social engineering
Social engineering is a major cyber threat to businesses of any size. But with a little effort, education, and investment, you can harden your organization’s cyber security.
User awareness of social engineering scams
User awareness is extremely important, but many organizations struggle in this area. Educating your team is essential to your defence, and you should focus on things like what social engineering is, how to recognize it, and what to do about it.
For training, educate employees on both technical and behavioural indicators of a social engineering scam. For example, technical indicators of a malicious email may include:
- Suspicious links— looking at the links and attachments in an email can expose its legitimacy. Typos in the domain names, and URLs that are long or complex, are suspicious.
- Suspicious attachments— look at the name of the file and the extensions. Doubling them up (important_work_files.doc.exe) is a popular tactic that attackers use.
Behavioural indicators, on the other hand, may include:
- Urgent requests— social engineers know that applying pressure is an advantage and they may thread in urgency as part of their attack.
- Changes to financial details or transactions— requests to change financial information can be common, but employees should remain cautious.
- Unusual or unexpected senders— receiving an email from someone you’ve never spoken to or worked with may be a sign of a social engineering attack.
- Changes in behaviour— a colleague writing differently or making unique requests may indicate that their account has been compromised.
Business processes
Having an alternate way to report cyber security concerns is important. If the hacker has gained access to an employee’s email account, they may be able to see and intercept the victim’s reporting of the attack. Consider creating a confidential instant messaging chat where conversation can happen quickly.
Organizations should have secondary checks in place to confirm that any changes to suppliers, vendors, providers, and financial details are legitimate. This can help to expose malicious behaviour before the damage is done.
Technical protections
Email account and cloud service monitoring can help you watch for suspicious behaviour in login events. Make sure that your organization has 24×7 cyber security monitoring in place to identify and address anomalies early before the attacker can cause serious damage or disruption.
Other technical protections like spam filtering can reduce risk further by blocking many malicious emails.
Test your employees’ resilience to social engineering
The most effective way to protect yourself against social engineering attacks is via simulation in a safe, controlled environment.
With Secure IT’s phishing campaigns, you get a fully researched and tailored campaign based on your organization’s unique needs. Every simulation mimics the techniques of modern social engineers and offers complete visibility of employee behaviour.
You receive a comprehensive report with campaign details, technical analysis, key findings — including baseline comparisons where applicable — and clear steps to improve your security posture and harden your organization against social engineering attacks.
Do you think phishing simulation training might be right for your business? Contact us at cybersecurity@secureits.ca
* * * * * *
Lyle Melnychuk is President and CEO of Secure IT Systems, an IT and security consulting firm specializing in cybersecurity consulting, cloud migration and business continuity solutions. For questions about how SIT can help your company be better prepared, contact lyle@secureits.ca or visit our website at www.secureits.ca






